This post tries to be a simple explanation of the Hide NAT and Static NAT concepts.
Given the following simple company network let’s see how this NAT types could fit in this scenario:
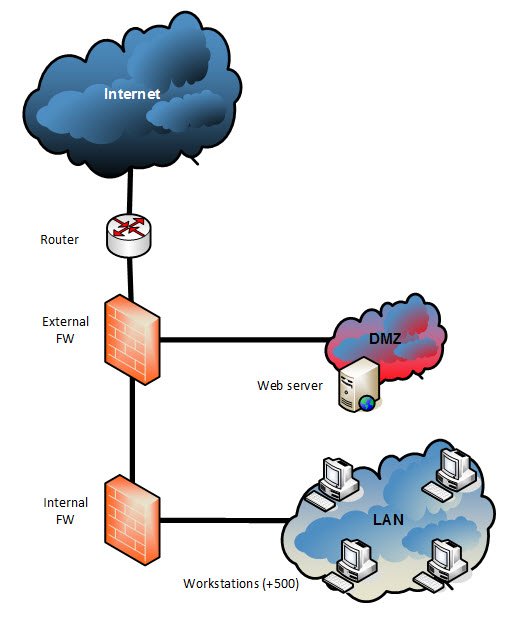
- We need the web server to be published, so it needs to be accesible from the Internet
- We need all the workstations to be able to browse the web, so they need to open connections to the Internet
Each of the computers, servers… have an assigned IP of their private Network.
But it is not possible to access the Internet by sending network packets with the private IP as source (obviously is only for private communications). They need to be referenced with a public IP that are provided by the ISP
Static NAT
For our first requirement (publish the webserver), we need a Static NAT:
A static NAT is a 1 to 1 mapping/translation of an IP address performed by the firewall so that:
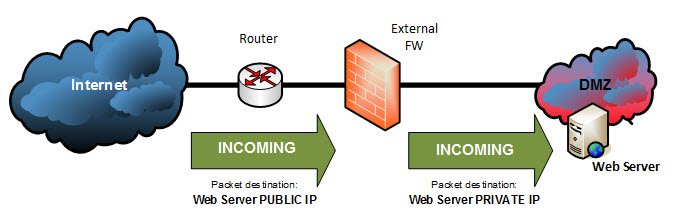
- the web server would be accesible from the Internet (incoming connections) a public IP address is translated to a private IP address
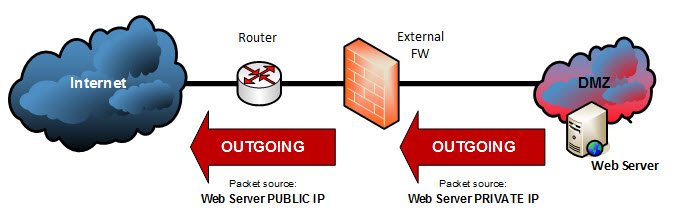
- the web server could access the Internet with its own public IP
a private IP address is translated to a public IP address (outgoing connection)
Configuring Static NAT in Checkpoint
When creating a network object like a server, in the General Properties the private IP is configured:
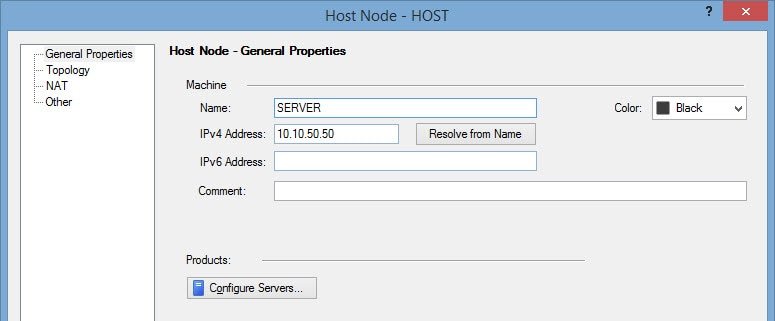
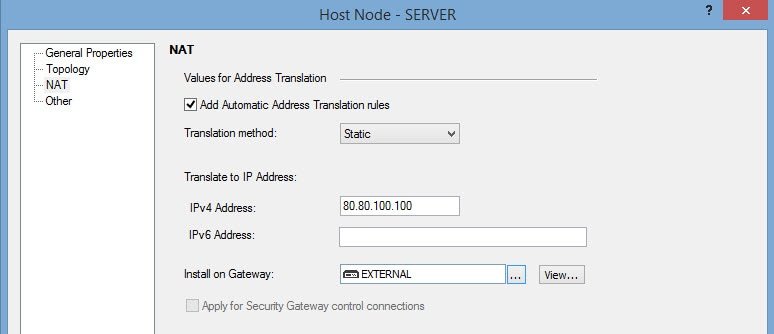
Then, the NAT tab allows us to configure either the Static or the Hide NAT.
The image shows how to assign a Static NAT with the 80.80.100.100 public IP address.
Hide NAT
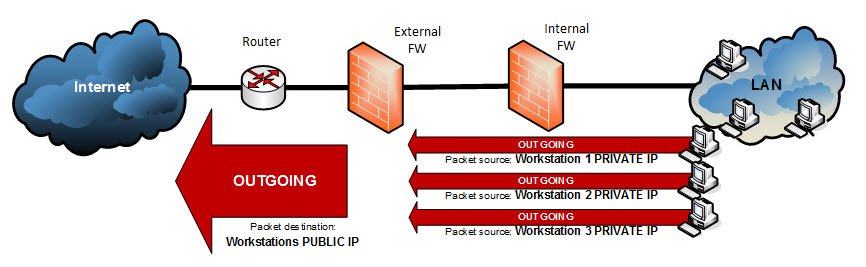
Allowing all the workstations access the Internet requires a Hide NAT
A Hide NAT is a many to 1 mapping/translation of IP address performed by the firewall so that:
- the workstations could access the Internet with the same public IP (outgoing connections)
many IP addresses are translated to a public IP address (outgoing connections)
- the workstations would NOT be accessible from the Internet (incoming connections)
a single public IP cannot be translated to many private IP addresses
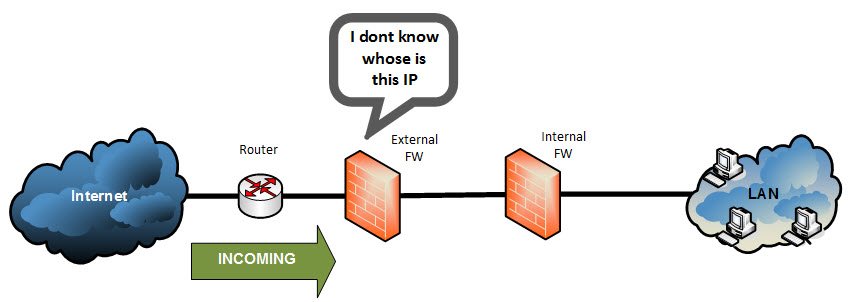
But how can the response packets be returned from the internet to the workstation?
If the workstations are not accesible from the Internet, how are the response packets received?
- Well, the workstations sends the first packet, the firewall registers on a “NAT table” the source Port and source IP (private).
- When it receives an incoming packet with destination the public IP used for Hide NAT, the firewall searches the “NAT table” for the destination port. If its a packet related to a previous one sent from the workstation it will find an entry in the table so that it can extract the related private IP address and perform the NAT.
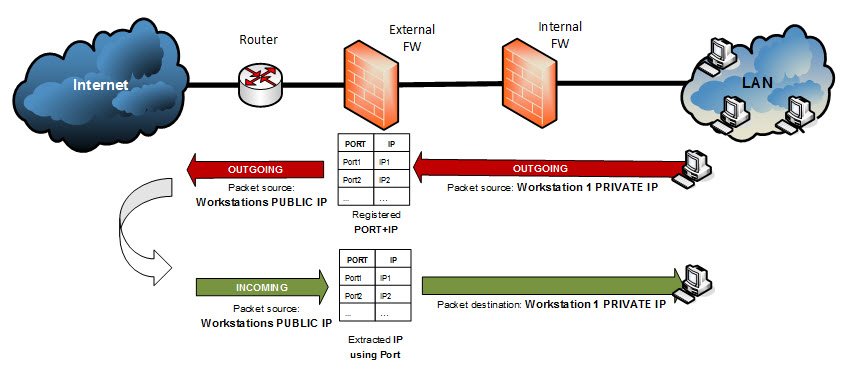
Obviously, when a machine in Internet tries to open a connection (send the first packet) to a Hide public IP, there is no related entry in the table so it is not a possible succesful scenario.
Why not use always Static NAT?
There are many workstations (let’s suppose this scenario has more than 500 for example). That implies we would need more than 500 public IPs, and given the IPv4 address exhaustion, the solution is the hide NAT method.
Anyway, we dont need to publish the workstations to the Internet.
Configuring Hide NAT in Checkpoint
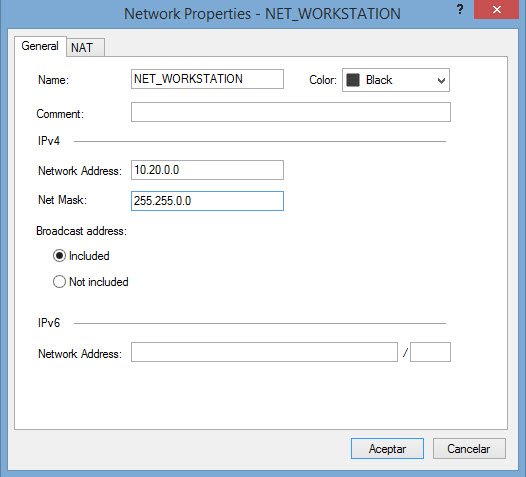
Like when creating a node object, in the General Properties of a network object the private IP range is configured:
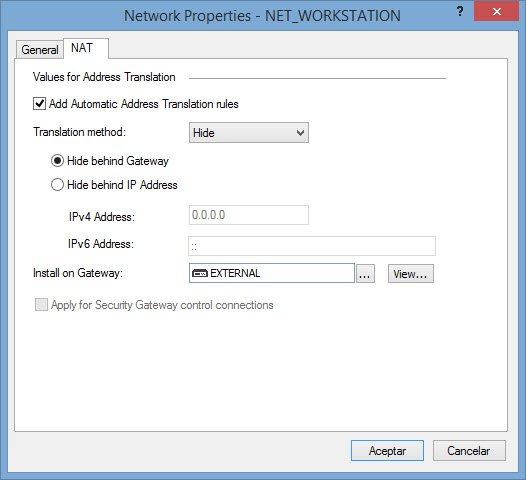
Then, the NAT tab allows us to configure Hide NAT by using the firewall IP or another one:
NAT in Checkpoint
Only some things to note before finishing the post:
Apply each NAT only on the gateway(s) you need
Its very important to apply the NAT section of the host only to the gateway we want (Instead of all, the default option)
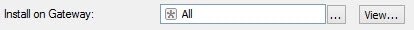
Otherwise, for example, in a VSX environment all VS firewalls can start to reply those ARP request, and so, steal packets among them.
Manual and automatic NAT
The examples showed in this post is the “automatic” method of NAT configuration in Checkpoint. But there is also a “manual” method.
Please, visit my post Checkpoint – Automatic NAT vs Manual NAT for details.