This post explains how to generate self signed certificates with SAN – Subject Alternative Names using openssl. It is a common but not very funny task, only a minute is needed when using this method.
The example below generates a certificate with two SubAltNames: mydomain.com and www.mydomain.com
Create openssl configuration file
Create configuration file for openssh (In a Linux system, I usually set /etc/ssl/selfsigned as working directory in which generate the config files and generated certificates…) called for example mydomain.cnf with the following parameters:
(This is not a general openssh configuration file. Only a “one-time” use)
[req]
default_bits = 2048
prompt = no
default_md = sha256
x509_extensions = v3_req
distinguished_name = dn
[dn]
C = ES
ST = MyState
L = MyCity
O = MyOrg
emailAddress = email@mydomain.com
CN = mydomain.com
[v3_req]
subjectAltName = @alt_names
[alt_names]
DNS.1 = mydomain.com
DNS.2 = www.mydomain.com
If no SAN is needed to be added, remove the red lines.
If more SAN names are needed, add more DNS lines in the [alt_names] section.
Run OpenSSL command
The command generates the certificate (-out) and the private key (-keyout) by using the configuration file (-config). The “-nodes” parameter avoids setting a password to the private key.
# openssl req -new -x509 -newkey rsa:2048 -sha256 -nodes -keyout mydomain.com.key -days 3560 -out mydomain.com.crt -config mydomain.com.cnf
Generating a 2048 bit RSA private key
..................................................+++
.+++
writing new private key to 'mydomain.com.key'
-----
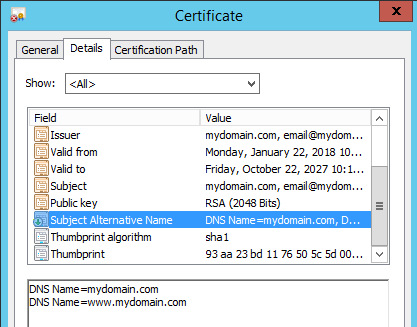
The generated certificate showing the SANs:
Example config in Apache:
You can use the generated certificate in any webserver.
For example to apply it in Apache, use the SSLCertificateFile and SSLCertificateKeyFile for both the cert and the private key:
<VirtualHost *:443>
ServerName mydomain.com
ServerAlias www.mydomain.com
ServerAdmin somoit@somoit.net
DocumentRoot "/var/www/html/myweb"
<Directory "/var/www/html/myweb/">
Options MultiViews FollowSymlinks
AllowOverride All
Order allow,deny
Allow from all
</Directory>
TransferLog /var/log/apache2/myweb_access.log
ErrorLog /var/log/apache2/myweb_error.log
SSLEngine on
SSLCertificateFile /etc/ssl/selfsigned/mydomain.com.crt
SSLCertificateKeyFile /etc/ssl/selfsigned/mydomain.com.key
</VirtualHost>
