Dont be afraid. Joining a linux machine to a windows active directory domain is not difficult. This post explains step by step how to join a Debian or Ubuntu linux machine but it can applied for other distributions without much different commands.
Install needed packages
Install realmd
apt-get install realmdIt may happen that the command returns an error like this:
sudo realm discover domain.com
realm: Couldn't discover realms: Not authorized to perform this actionTo fix it install the policykit-1 packagesudo apt-get install policykit-1
Now it should return something like this:
sudo realm discover domain.com
domain.com
type: kerberos
realm-name: DOMAIN.COM
domain-name: domain.com
configured: no
server-software: active-directory
client-software: sssd
required-package: sssd-tools
required-package: sssd
required-package: libnss-sss
required-package: libpam-sss
required-package: adcli
required-package: samba-common-binInstall more required packages
As you can see in the output of the “realm discover” command, there are some packages needed to allow joining the windows domain. So, run the command:
apt-get install sssd-tools sssd libnss-sss libpam-sss adcli samba-common-binCommand to join the domain
if you read the manpages of the realm command, there is a “join” action with some parameters i think very interesting:
–computer-ou=OU=xxx
The distinguished name of an organizational unit to create the computer account. The exact format of the distinguished name depends on the client software and membershipsoftware. You can usually omit the root DSE portion of distinguished name. This is an Active Directory specific option.
F.e: –computer-ou=OU=SERVERS
–os-name=xxx
The name of the operation system of the client. When joining an AD domain the value is store in the matching AD attribute.
F.e: –os-name=`uname -o`
–os-version=xxx
The version of the operation system of the client. When joining an AD domain the value is store in the matching AD attribute.
F.e: –os-version=`uname -rsv`
sudo realm join domain.com -U 'user1' --computer-ou=OU=SERVERS --os-name="`uname -o`" --os-version="`uname -rsv`" --install='/' --verbose The –install=’/’ in case just in case it returns an error saying it cannot find the required packages (altough they were installed in the previous section).
Maybe you will see something like this as output:
$ sudo realm join domain -U 'user1' --computer-ou=OU=SERVERS--os-name="`uname -o`" --os-version="`uname -rsv`" --install='/' --verbose
* Resolving: _ldap._tcp.domain.com
* Performing LDAP DSE lookup on: 192.168.194.1
* Performing LDAP DSE lookup on: 192.168.194.3
* Successfully discovered: domain.com
Password for user1:
* Assuming packages are installed
* LANG=C /usr/sbin/adcli join --verbose --domain domain.com --domain-realm DOMAIN.COM --domain-controller 192.168.194.1 --computer-ou OU=SERVERS,dc=domain,dc=com --os-name GNU/Linux --os-version Linux 4.19.0-5-amd64 #1 SMP Debian 4.19.37-5+deb10u2 (2019-08-08) --login-type user --login-user user1 --stdin-password
* Using domain name: domain.com
* Calculated computer account name from fqdn: LABDEBIAN
* Using domain realm: domain.com
* Sending netlogon pings to domain controller: ldap://192.168.194.1
* Received NetLogon info from: DC1.domain.com
* Wrote out krb5.conf snippet to /var/cache/realmd/adcli-krb5-o4dezD/krb5.d/adcli-krb5-conf-9pCpsi
* Authenticated as user: user1@domain.com
* Looked up short domain name: DOMAIN
* Using fully qualified name: labdebian
* Using domain name: domain.com
* Using computer account name: LABDEBIAN
* Using domain realm: domain.com
* Calculated computer account name from fqdn: LABDEBIAN
* Generated 120 character computer password
* Using keytab: FILE:/etc/krb5.keytab
* Computer account for LABDEBIAN$ does not exist
! Couldn't find a computer container in the ou, creating computer account directly in: OU=SERVERS,dc=domain,dc=com
* Calculated computer account: CN=LABDEBIAN,OU=SERVERS,dc=domain,dc=com
* Created computer account: CN=LABDEBIAN,OU=SERVERS,dc=domain,dc=com
* Set computer password
* Retrieved kvno '2' for computer account in directory: CN=LABDEBIAN,OU=SERVERS,dc=domain,dc=com
* Modifying computer account: dNSHostName
* Modifying computer account: userAccountControl
* Modifying computer account: operatingSystem, operatingSystemVersion, operatingSystemServicePack
* Modifying computer account: userPrincipalName
! Couldn't set service principals on computer account CN=LABDEBIAN,OU=SERVERS,dc=domain,dc=com: 00002083: AtrErr: DSID-03151785, #1:
0: 00002083: DSID-03151785, problem 1006 (ATT_OR_VALUE_EXISTS), data 0, Att 90303 (servicePrincipalName)
* Discovered which keytab salt to use
* Added the entries to the keytab: LABDEBIAN$@DOMAIN.COM: FILE:/etc/krb5.keytab
* Added the entries to the keytab: host/LABDEBIAN@DOMAIN.COM: FILE:/etc/krb5.keytab
* Added the entries to the keytab: host/labdebian@DOMAIN.COM: FILE:/etc/krb5.keytab
* Added the entries to the keytab: RestrictedKrbHost/LABDEBIAN@DOMAIN.COM: FILE:/etc/krb5.keytab
* Added the entries to the keytab: RestrictedKrbHost/labdebian@DOMAIN.COM: FILE:/etc/krb5.keytab
* /usr/sbin/update-rc.d sssd enable
* Successfully enrolled machine in realmIf you get the same error (“Couldn’t set service principals…“), the reason is the hostname is not set with the domain. To fix it:
– Edit /etc/hostname –> (f.e.) labdebian.domain.com
– Apply running this command or reboot –> (f.e.) hostnamectl set-hostname labdebian.domain.com
The related active directory should has been succesfully created:
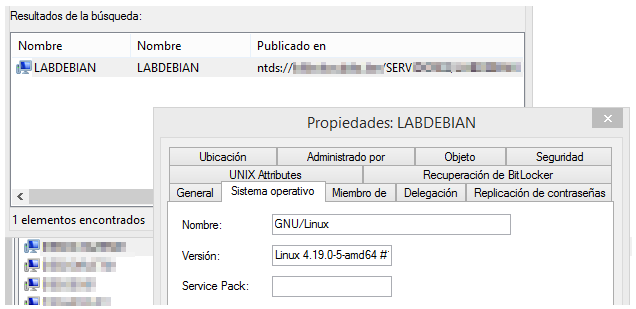
Check the machine has joined succesfully
sudo realm list
domain.com
type: kerberos
realm-name: DOMAIN.COM
domain-name: domain.com
configured: kerberos-member
server-software: active-directory
client-software: sssd
required-package: sssd-tools
required-package: sssd
required-package: libnss-sss
required-package: libpam-sss
required-package: adcli
required-package: samba-common-bin
login-formats: %U@domain.com
login-policy: allow-realm-loginsConfigure permissions to login
Permit every domain user:
sudo realm permit --realm domain.com --allDeny everyone but the members of the group:
sudo realm deny -R domain.com -a
sudo realm permit -R domain.com -g SYSADMINSLogin with a domain account
Now you should be able to login with a domain account using user@domain format:
login as: user1@domain.com
user1@10.200.0.10's password:
Linux labdebian 4.19.0-5-amd64 #1 SMP Debian 4.19.37-5+deb10u2 (2019-08-08) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Wed Dec 4 11:06:15 2019 from 10.50.12.43
user1@labdebian:~$In case you get this error…
Could not chdir to home directory /home/user1@domain.com: No such file or directoryrun this command and the next time you login it will be fixed and the /home/<user>@<domain> home path will be generated:
sudo echo 'session required pam_mkhomedir.so skel=/etc/skel umask=0022' >> /etc/pam.d/common-session
Avoid inserting domain when logging
You can change the login format by editing the /etc/sssd/sssd.conf file. Set this parameter to false:
use_fully_qualified_names = FalseAfter restarting the sssd service you will be able to login inserting only the user (without the domain).
