HTTP Strict Transport Security (HSTS) is a security feature that allows websites to specify that browsers should only interact with them over secure HTTPS connections. By sending an HSTS header with a specified max-age directive, websites instruct browsers to automatically convert all HTTP requests to HTTPS, thereby enhancing security and protecting against various attacks, such as SSL-stripping attacks.
You can check your site by using a site like SSL Labs (https://www.ssllabs.com/ssltest/) or SecurityHeaders (https://securityheaders.com/) to perform a comprehensive security assessment of your website that evaluates various security aspects of the SSL/TLS configuration, including the presence and correctness of HSTS headers.
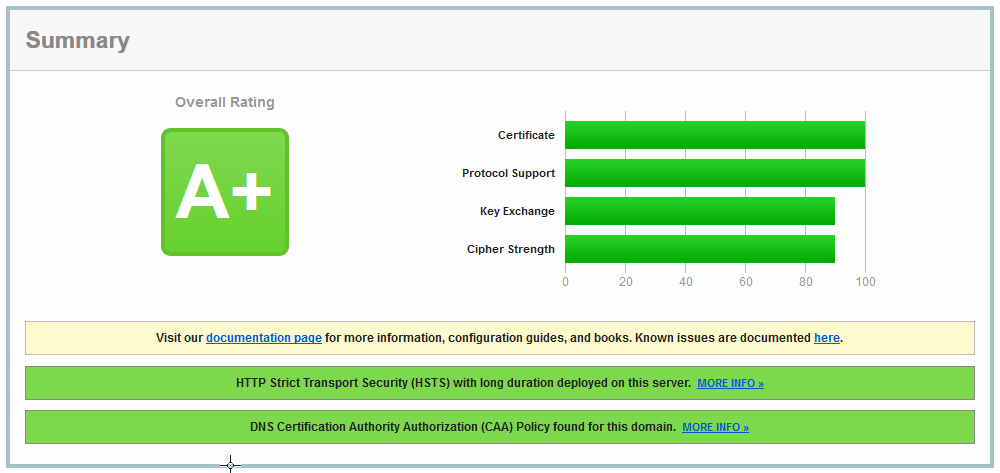
For example, this is the result of checking an example site I published using F5:
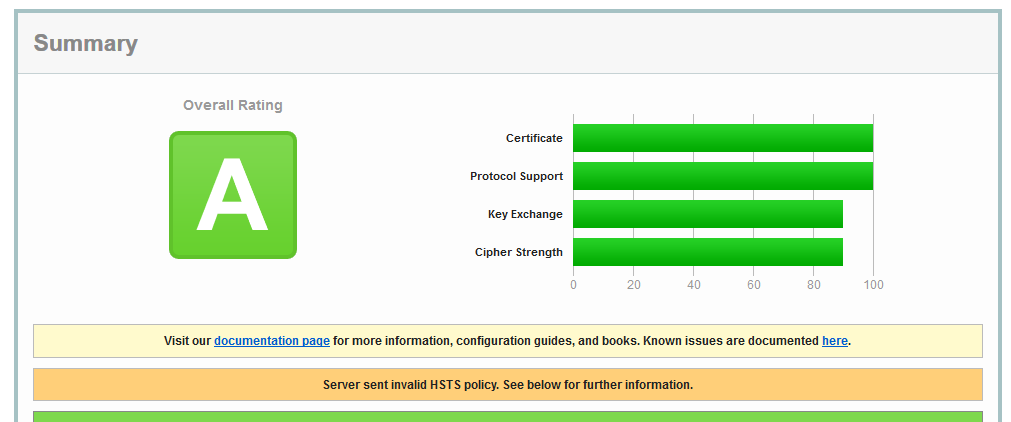
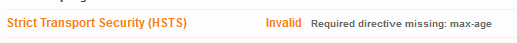
As you can see, it returns an invalid HSTS header: "Required directive missing: max-age"
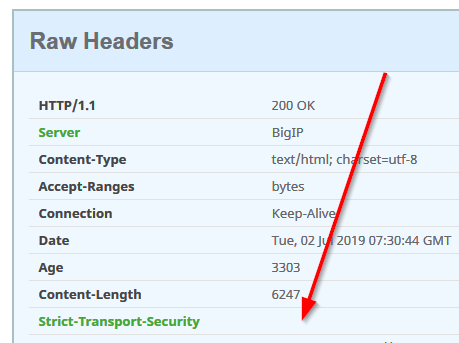
That header was sent by the web backend behind the F5 device.
The official article https://support.f5.com/csp/article/K04436209 shows the way to make F5 insert the HSTS header.
when HTTP_RESPONSE_RELEASE {
if {!([HTTP::header exists “Strict-Transport-Security”])}
{
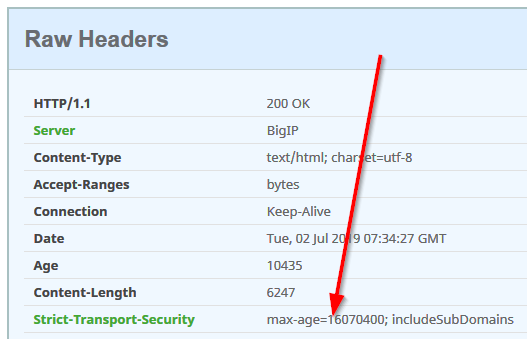
HTTP::header insert “Strict-Transport-Security” “max-age=16070400; includeSubDomains”
}
}But that was not valid for the scenario I came across because the F5 header was already sent by another device and without the required max-age value.
Instead of inserting, by using this irule the HSTS was correctly set...
when HTTP_RESPONSE_RELEASE {
HTTP::header replace “Strict-Transport-Security” “max-age=16070400; includeSubDomains”
}...as confirmed afterwards: