In certain scenarios it can be interesting or necessary to apply SNAT only to certain client IPs when accesing a virtual server to f.e. avoid assymetric routes, when the server gateway is not the F5… (take a look at this link for more examples).
These are the steps (im using BIG IP v13)…
Create a SNAT pool
I prefer the SNAT to be applied by using certain IP, so I have to create a SNAT pool.
Local Traffic – Address Translation – SNAT Pool List – <Create>
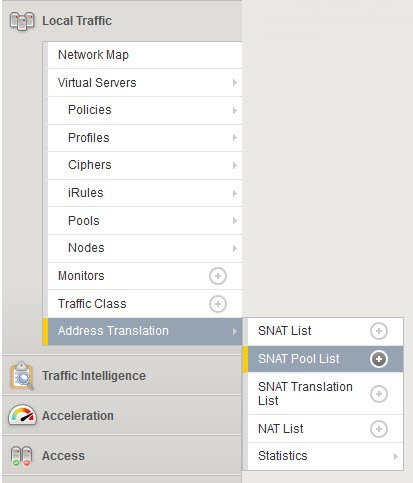
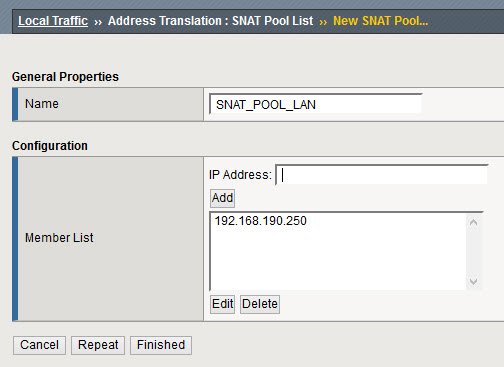
Assign name and iP(s) to use as translated source IP
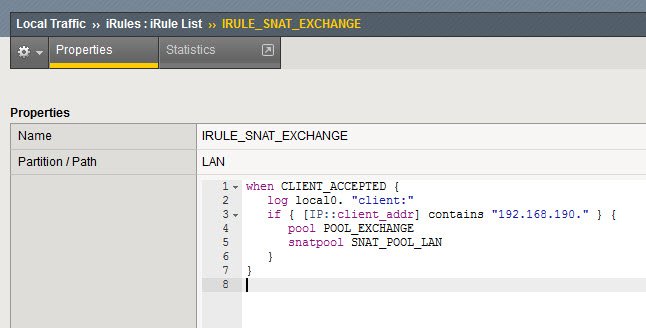
Create IRULE
Before creating the IRULE we need to know 3 “values”:
– client IP(s) to which we want to apply the SNAT
– Name of the virtual server POOL of the virtual server we want the SNAT to apply to
– Name of the SNAT POOL created on the previous step
Local Traffic – IRules – IRule List – <Create>
Assign name and set the following code (in red my own example values. Replace them with yours)
when CLIENT_ACCEPTED {
log local0. "client:"
if { [IP::client_addr] contains "192.168.190." } {
pool POOL_EXCHANGE
snatpool SNAT_POOL_LAN
}
}
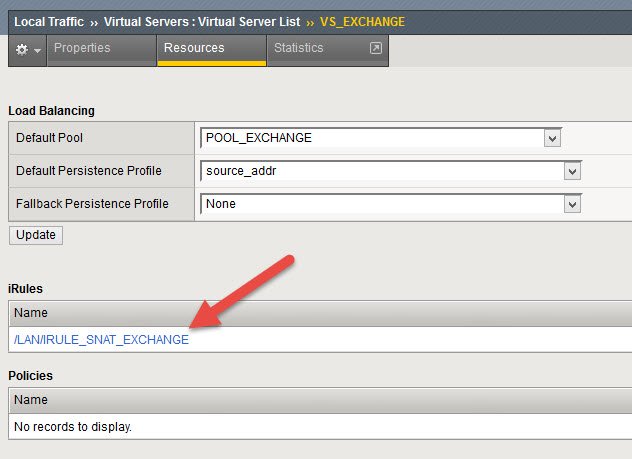
Assign IRULE to POOL
Local Traffic – Virtual Servers – Virtual Server List – <Select VS> – Resources
Assign the newly created IRule in the IRules section
Check IRULE is working correctly
Command “show sys conn”
By using the “show sys conn” TMSH command you can check active connection (filtering by virtual server IP for example).
For example, my VS_EXCHANGE virtual server has an 192.168.206.233 IP.
To check the connections:
# tmsh show sys conn cs-server-addr 192.168.206.233%1
The ouput shows: <original client IP> <virtual server IP> <translated client IP> <server IP>
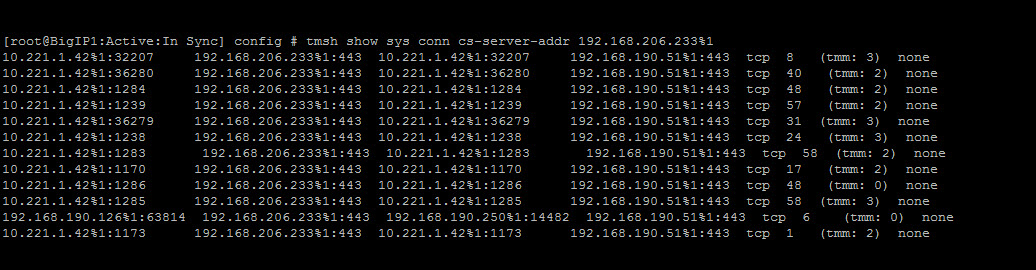
As you can see, when the client IP does not contain “192.168.190.”, the IP is not translated.
However, the “192.168.190.126” client IP was translated to the one defined in the SNAT pool (192.168.190.250).
Log file /var/log/LTM
/var/log/ltm file can also show if the IRule is being applied:
# tail -f /var/log/ltm | grep IRULE_SNAT_EXCHANGE
Aug 17 10:24:05 BigIP1 info tmm3[28767]: Rule /LAN/IRULE_SNAT_EXCHANGE <CLIENT_ACCEPTED>: client:
Aug 17 10:24:05 BigIP1 info tmm2[28767]: Rule /LAN/IRULE_SNAT_EXCHANGE <CLIENT_ACCEPTED>: client:
