By default F5 BigIp configuration utility uses local users to authenticate.
But if your enviroment allows it, using another way like Active Directory, LDAP, RADIUS might be very interesting. This post focuses in Active Directory but, anyway, it can point you and be a great help to configure for another type of server.
So, follow these easy steps:
Configure Active Directory settings
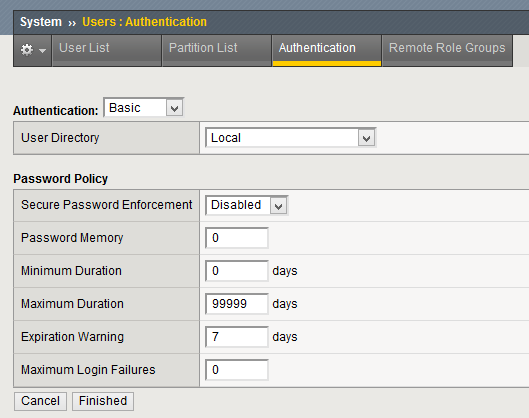
In the “Users – Authentication” section, set the “User Directory” value to “Remote – Active Directory”
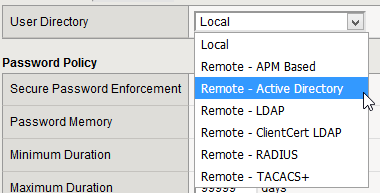
In the “Authentication” tab, “Authentication” section fill the multiple fields as I explain below:
- Host + Port
Your DC server (or domain if resolves to your multiple DCs) and the port (Im not using LdapS so 389 in my case).
- Remote Directory Tree + Scope
OU in which the users that will authenticate will be located. Depending on the scope, limited to that location, one level or any subfolder under that location.
- Bind
DN and password of the user that will be used to perform the binding (connection to the active directory to be able to read it).
To check connection and binding manually:
[root@BigIP1:Active:Changes Pending] config # ldapsearch -xLLL -H 'ldap://domain.com' -b "dc=domain,dc=com" -D domain\\ADservice -w 'secret' '(samaccountname=user1)'
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: user
cn: User 1
...- Check Member Attribute in Group
Enable it to make F5 know for each user which groups is member of.
- Role
The default role applied to the users found in the “Remote Directory Tree”. I choosed “No access” because I only want to allow authentication to the Active Directory users that are member of the groups created to grant this permission (like you’ll see right now).
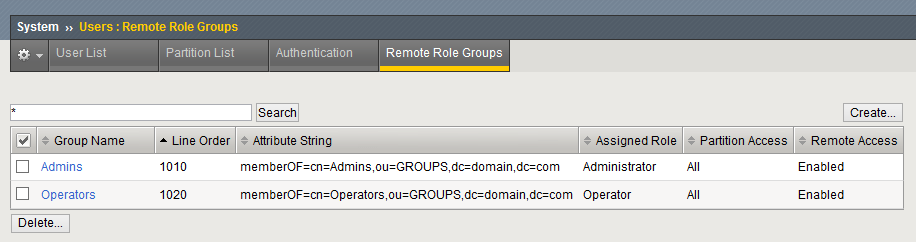
Configure Role Groups
Create groups that will be associated to roles on your AD:
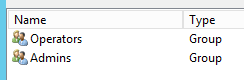
In the “Remote Role Groups” tab, create the groups you want, setting the CN of the group and role you associate. For example:
Test!
Add members to your groups and test it!