Check Point Identity Awareness module provides visibility into network traffic, allowing organizations to enforce security policies based granular control over user access.
Recently, I encountered a puzzling issue where the Identity Awareness module integrated with Active Directory (AD) began generating persistent errors, disrupting network operations. Upon investigation, I discovered that these errors were evident in the logs, revealing a continuous stream of "Failed Login" events. Here's how I tackled the problem and restored functionality.
Identifying the Issue
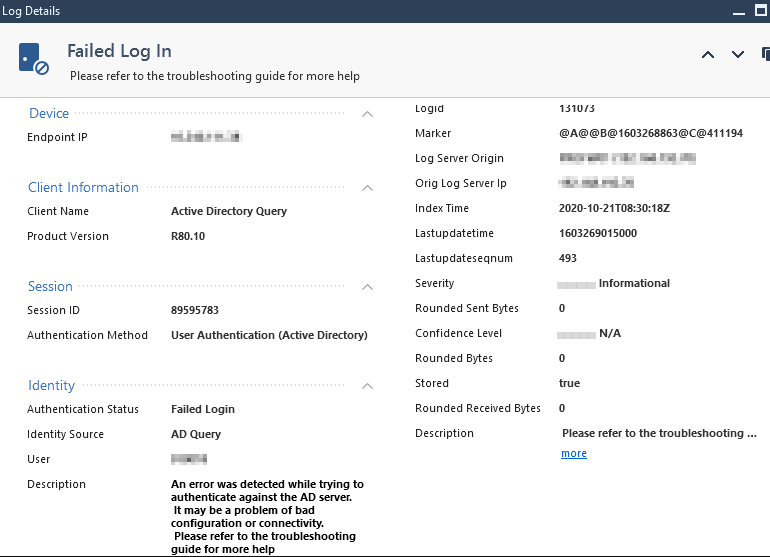
The first step was to scrutinize the logs, where I found a plethora of "Failed Login" entries, indicating authentication challenges. This prompted a deeper dive into the configuration settings to pinpoint the root cause.
Troubleshooting and Solution
After meticulous investigation, I determined that several settings defined in the Account Unit required attention to rectify the issue:
- Check Username/Password: Ensure that the credentials are accurate and up-to-date. Incorrect credentials can lead to authentication failures and subsequent errors.
- Verify Branch Configuration: Validate that the Branch configuration under the "Object Management" tab is correctly configured. Misconfigurations here can impede communication with AD and result in authentication issues.
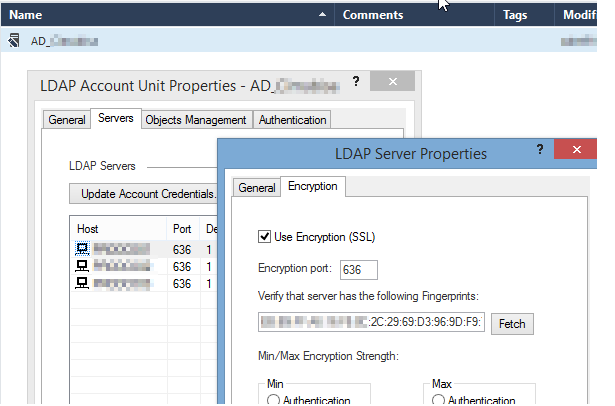
- LDAPS Certificate Verification: If LDAPS (LDAP over SSL/636) is utilized, verify whether the certificate has changed. In case of certificate modifications, re-fetch the fingerprint to ensure secure communication:
- Navigate to the Servers tab.
- Access the servers and proceed to the Encryption tab.
- Click "Fetch" to retrieve the updated fingerprint.
- Repeat this process for all relevant servers.
- After refetching all servers, install the relevant policies
Resolution and Mitigation
Upon performing the necessary steps, including the re-fetching of fingerprints and policy installations, the persistent errors were successfully resolved.