This time I show you the Checkpoint “Application Control Signature Tool”. This tool allows you to create your own Apps and URL filtering signatures.
For example, I’m using it to block Torrent clients based on the User-Agent, but it is very versatile and you can use it in many ways.
Contents
- 1 Downloading the tool
- 2 Usage
- 2.1 Main menu
- 2.2 Scenarios
- 2.3 Export application
- 2.4 Import Application
- 3 Usage example (Bittorrent clients)
Downloading the tool
Visit the following SK103051 and download it. This post explains the GUI tool, but it also exists the command-line version.
SK103051 – Signature Tool for custom Application Control and URL Filtering applications
Usage
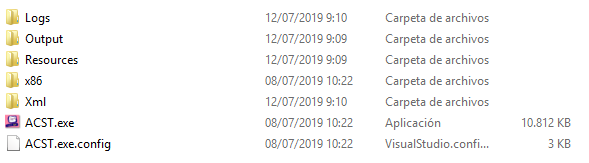
After uncompressing the downloaded ZIP file, run ACST.exe
Main menu
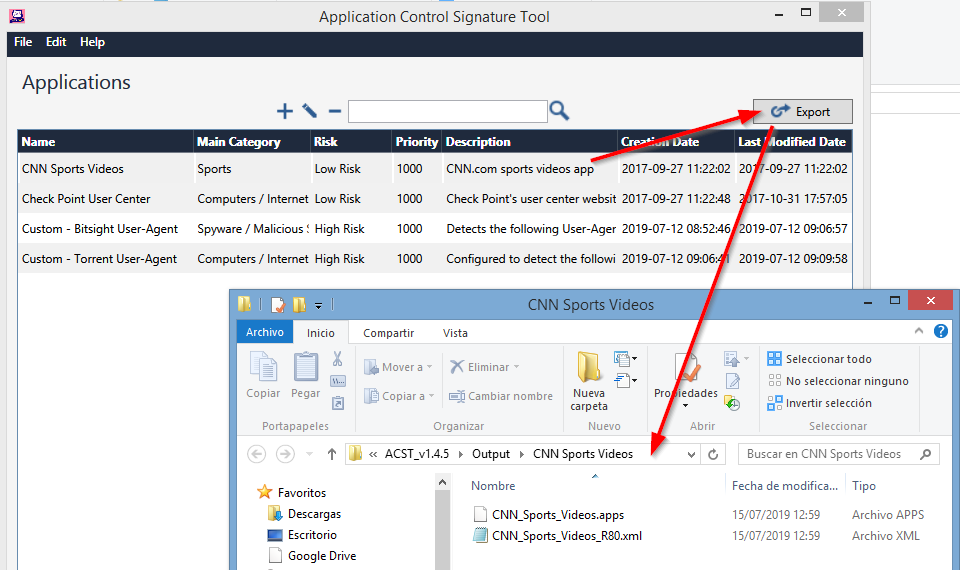
The application comes with 2 preconfigured custom Apps as the image shows.
In the main menu you can create/delete new Applications, edit the existing ones, export them…
Scenarios
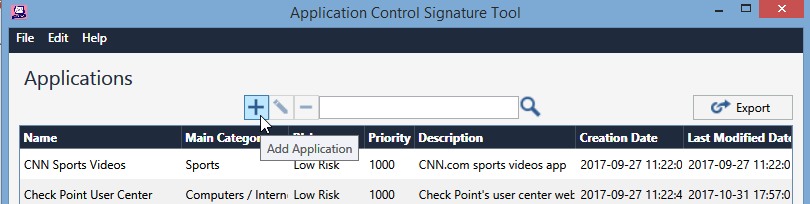
After pressing the “+” button to add a new Application, you can see the mandatoty fields in red (Name, Category, Risk, Description). But the fun is in the “Application Scenarios” window.
The scenarios can be of different types (HTTP request, SSL/TLS, IP, Raw data…)
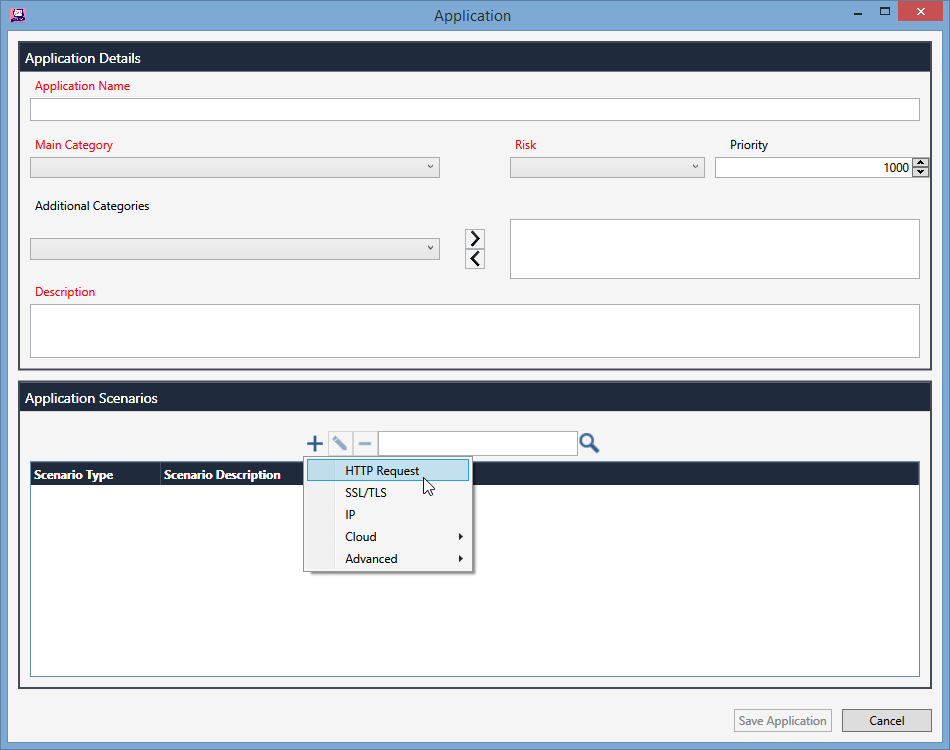
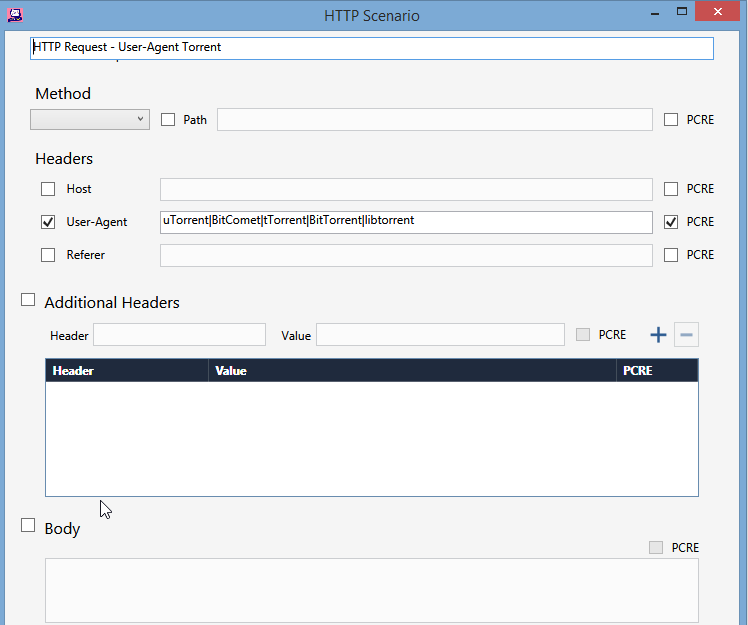
Each scenario has the related parameters. For example, the HTTP request scenario offers the Method, Headers like Host, User-Agent, Referer, or the Header you want (Addtional Headers), body…
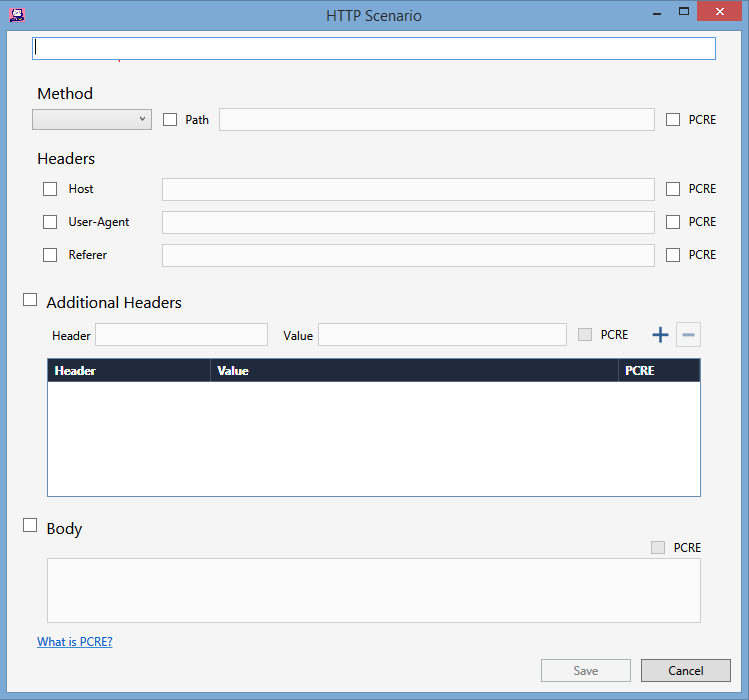
Fields for Raw Data
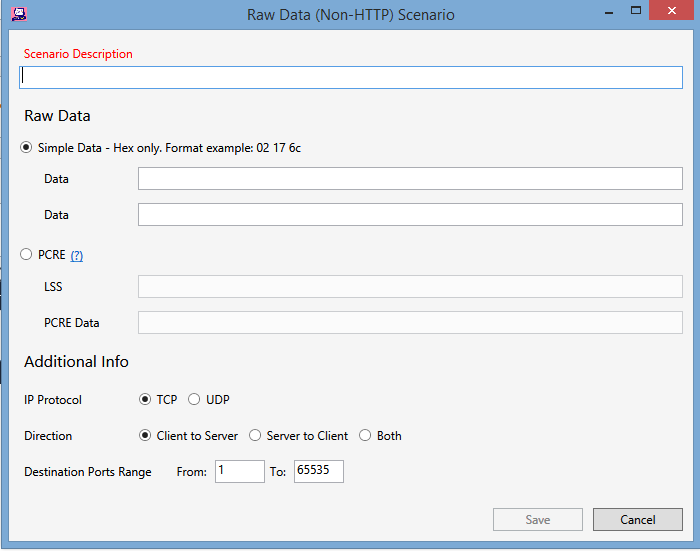
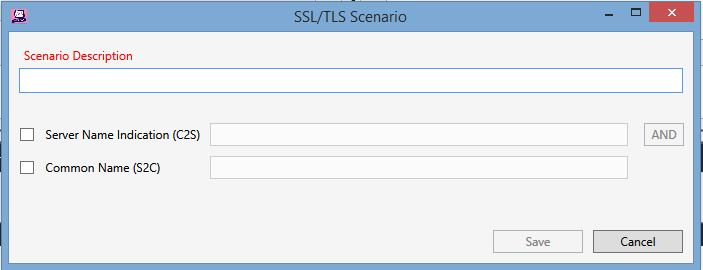
Fields for SSL/TLS
Export application
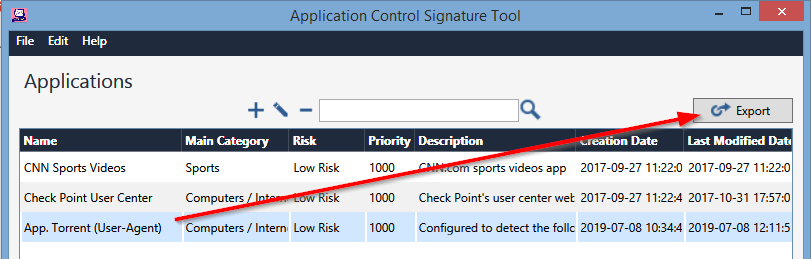
In the main manu, select one of the existing Applications and press the “Export” button.
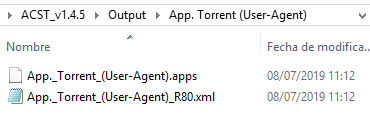
Automatically a new window is opened where the a .xml and .apps file are created.

Those files are the ones needed to import the new Application to our Checkpoint policy / database.
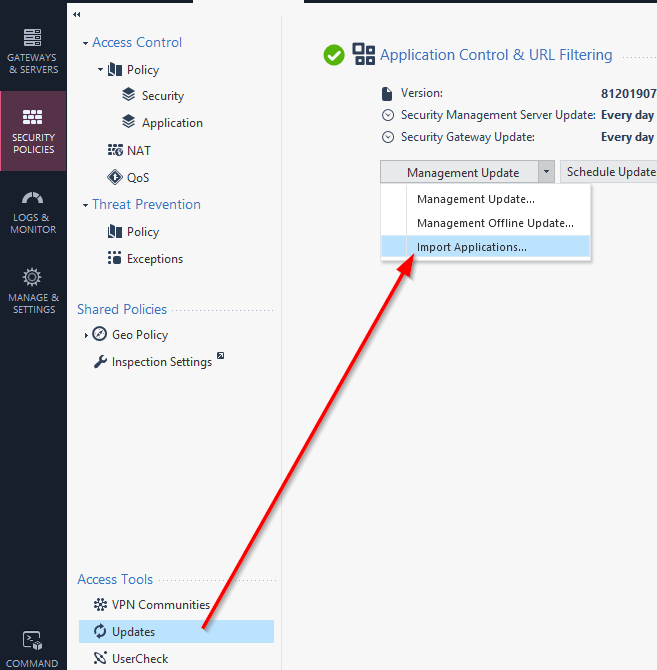
Import Application
In my R80.10 I find the “Import Applications” option in the “Updates” section of the “Application Control & URL Filtering”
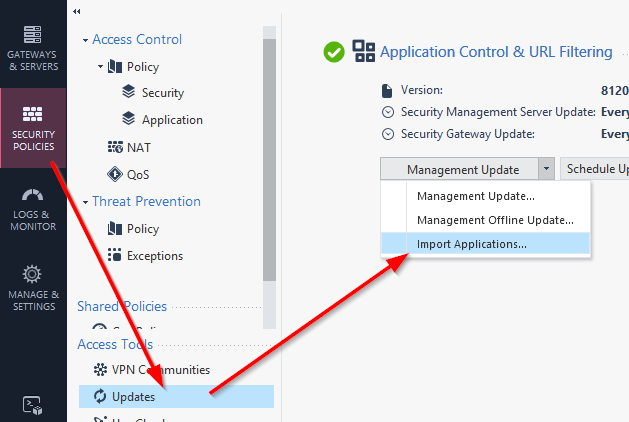
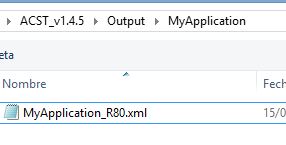
Select the related .XML to import it
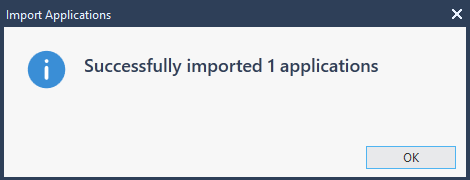
Now, the new Application is available to be used in the Application Policy.
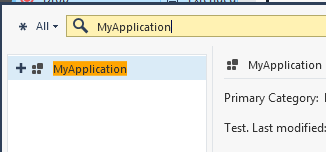
Usage example (Bittorrent clients)
Altough I am using the Checkpoint Bittorent objects…
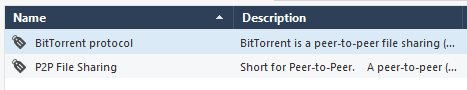
…in some cases, there are still outbound torrent connections that are not filtered.
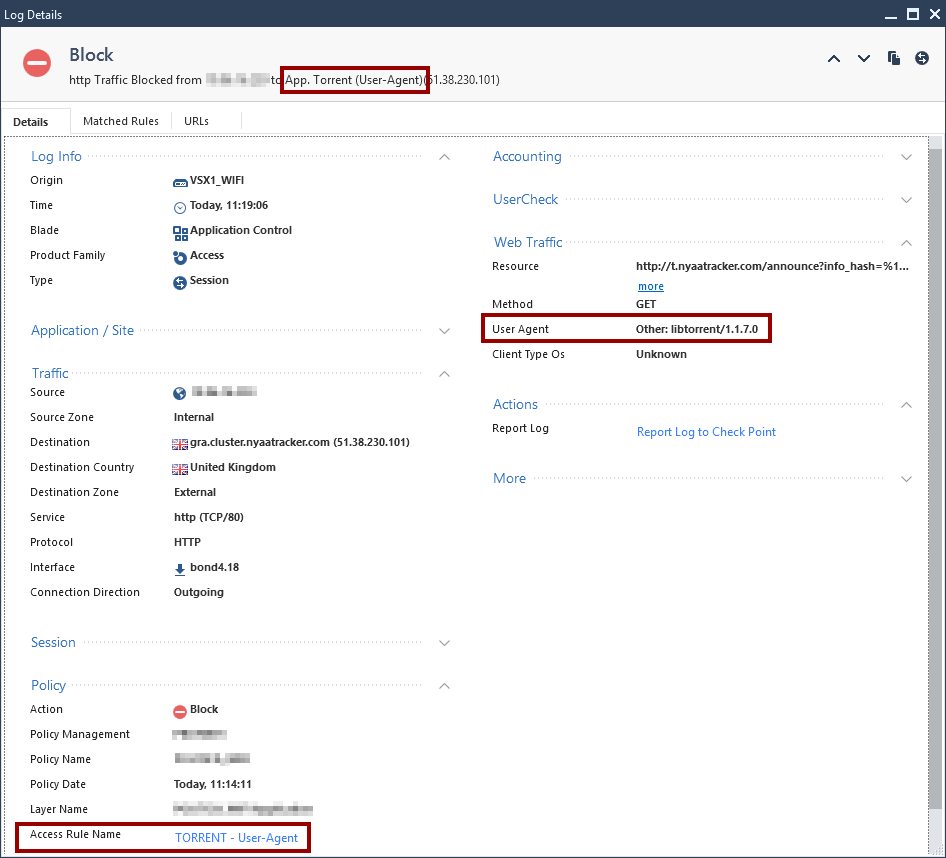
To fix it i tried to use a custom application and it seems to work. The idea is, based on values of the User-Agent that are related to Torrent clients, filter those connections.
Simply check the “User-Agent” field, fill it with the values of torrent clients (uTorrent|BitComet|tTorrent|BitTorrent|libTorrent) separated by pipes and also check the PCRE to enable regex expressions).
The export process…
The import process…
Configure a rule that drops the custom Application
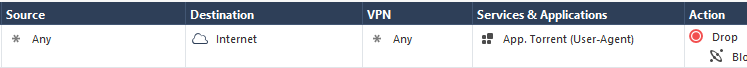
And, as the logs shows, connections that send any of those User-Agent header values are dropped