However, despite efforts to create strong passwords, sometimes they can be compromised. In this blog post, we'll delve into the process of cracking Windows machine passwords, shedding light on the methods used and the tools involved.
Tools we will use
- pwdump: A utility for dumping password hashes from the SAM database on Windows systems.
Link: website
Link: pdump8-8.2.zip - John the Ripper: A powerful password cracking tool that supports various cracking techniques and hash formats. Usually used under linux, in this example we are using the windows version.
Link: website
Link: john-1.9.0-jumbo-1-win64.zip - "rockyou" wordlist: A commonly used wordlist containing millions of passwords, useful for dictionary attacks. You can find it in many sites.
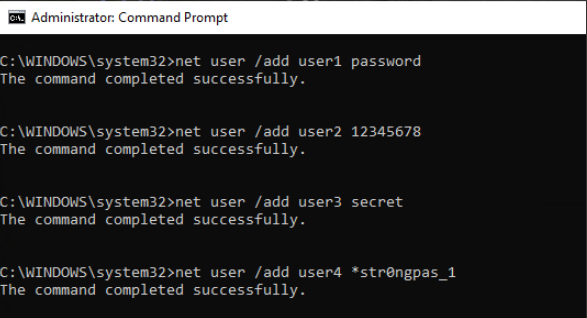
Link: rockyou.txt - Test users: This is not a tool but i created some users in my windows machine as test users to try to crack their passwords. The first 3 ones are weak passwords. The last one is an strong password.
Extracting Password Hashes
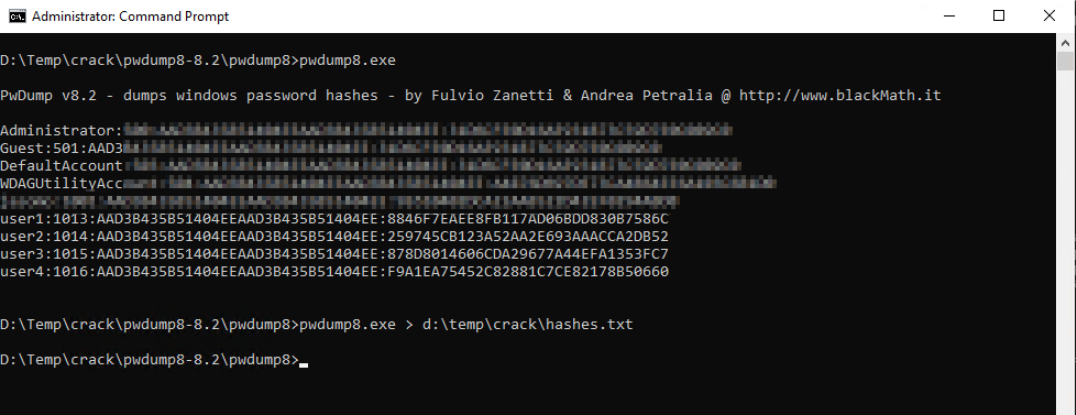
The first step in cracking Windows machine passwords involves extracting the password hashes from the system. One common tool for this purpose is pwdump. This utility allows users to dump the password hashes stored in the Security Account Manager (SAM) database on a Windows system. Obviously you need to be Administrator of the machine.
To extract the password hashes using pwdump, follow these steps:
- Download and unzip the pwdump zip file on your Windows machine.
- Open a command prompt with administrative privileges.
- Navigate to the directory where pwdump was unzipped.
- Run the command "pwdump8.exe" (8 because this is the version i am using the moment i am publishing this post) to extract the password hashes.
Cracking Password Hashes
Once the password hashes have been extracted, the next step is to crack them using a password cracking tool. One of the most popular tools for this purpose is John the Ripper. This powerful tool supports various password hash formats and employs different cracking techniques, including dictionary attacks, brute force attacks, and hybrid attacks.
Run John the Ripper with the appropriate options and specify the path to the password hash file. Use the "rockyou" wordlist for more comprehensive cracking.
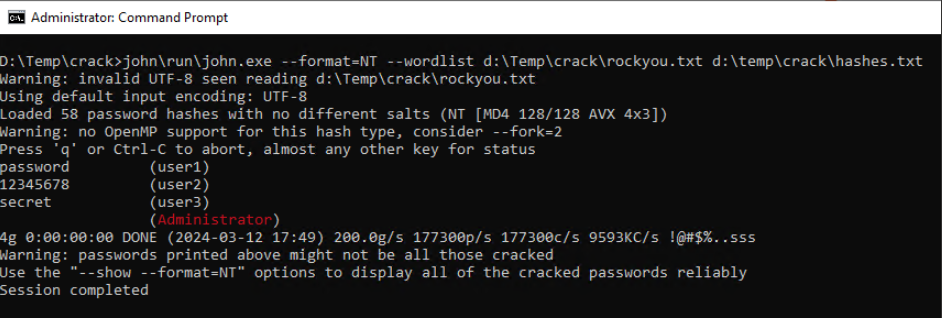
Check the path and the options in the example:
- The executable "john.exe" is under the run subfolder of the unzipped file you have downloaded
- --format-NT parameter to crack windows hashes
- --wordlist <path to rockyou.txt file> to use the wordlist
- last parameter is the hashes file we have generated in the previous step
As you can see, the passwords of user1, user2 and user3 have been cracked.
It was not possible to crack the strong password of user4.
It's important to note that the success of password cracking depends on various factors, including the strength of the passwords, the quality of the password cracking dictionary (such as "rockyou"), and the computational resources available.
Conclusion
In this blog post, we've explored the process of cracking Windows machine passwords, from extracting the password hashes using pwdump to cracking them using John the Ripper with the "rockyou" wordlist.
While password cracking can be a powerful tool for security professionals and penetration testers, it's essential to use these techniques responsibly and ethically. Additionally, organizations and individuals should prioritize strong password practices to mitigate the risk of password compromise.
